† Corresponding author. E-mail:
Supported by the National Natural Science Foundation of China under Grant Nos. 61402275, 61402015, 61273311, the Natural Sci- ence Foundation of Shaanxi Province under Grant Nos. 2015JM6263, 2016JM6069 and the Fundamental Research Funds for the Central Universities under Grant No. GK201402004
A practical E-payment protocol is presented in this paper. It is based on quantum multi-proxy blind signature. Adopting the techniques of quantum key distribution, one-time pad and quantum multi-proxy blind signature, our E-payment system could protect user’s anonymity as the traditional E-payment systems do, and also have unconditional security, which the classical E-payment systems can not provide. Furthermore, compared with the existing quantum E-payment systems, this practical system could not only support mobile E-payment transactions but also inter-bank transactions.
Today, E-commerce is favored by the majority of individuals for its convenience and speediness with technological advancements. Hence, it is particularly important to choose an appropriate model of payment. In 1983, Chaum proposed the first concept of E-cash.[1] Subsequently, E-cash system has attracted much attention and researchers proposed a number of E-cash payment schemes.[2–6] However, the security of the most existing E-cash payment schemes depends on some computational problems, which may be not difficult to solve with quantum algorithms.[7–8] The application of quantum signature in E-payment has attracted much attention because that the security of quantum cryptography relies on the principles of quantum mechanics.
In 2010, Wen and Nie proposed an E-payment system based on quantum blind and group signature, employing two TTPs (Third Trusted Party) to enhance the system’s robustness.[9] In succession, Wen et al. proposed an inter-bank E-payment protocol based on quantum proxy blind signature.[10] However, Cai et al.[11] showed that the dishonest merchant can succeed to change the purchase information of the customer in this protocol. In 2017, Shao et al.[12] proposed an E-payment protocol based on quantum multi-proxy blind signature. However, these protocols can not be applied to the business transactions, which use mobile E-payment. In real life, there are many business transactions need mobile E-payment, such as pos terminals. And an E-payment system supports secure mobile transactions is desired from the view of practical application.
In this paper, we proposed a new E-payment protocol to solve the problem and not only support secure mobile business transactions but also secure business transactions between two different banks. In our system, quantum multi-proxy blind signature is adopted to implement mobile payment and inter-bank payment. To the best of our knowledge, this is the first time to proposed a mobile quantum E-payment scheme, which not only supports mobile payment and inter-bank payment but also enhances the transaction credibility and the success of business rate. The property of multi-proxy blind signature could protect the anonymity of E-payment system, while the quantum signature could guarantee unconditionally security. Our scheme only needs Bell state measurement, which can be easily implemented under the current experimental conditions.
In this section, we introduce the basic theories of the quantum multi-proxy blind signature.
Proxy signature allows a designated person, called proxy signer, to sign on behalf of an original signer.[13] As for blind signature,[14] the message owner could get the authentic signature for his own message, but not reveal the specific content of the message. In some cases, such as an inter-bank trading system, both the property of proxy and blind signature are required for application and security concern, so multi-proxy blind signature was proposed.
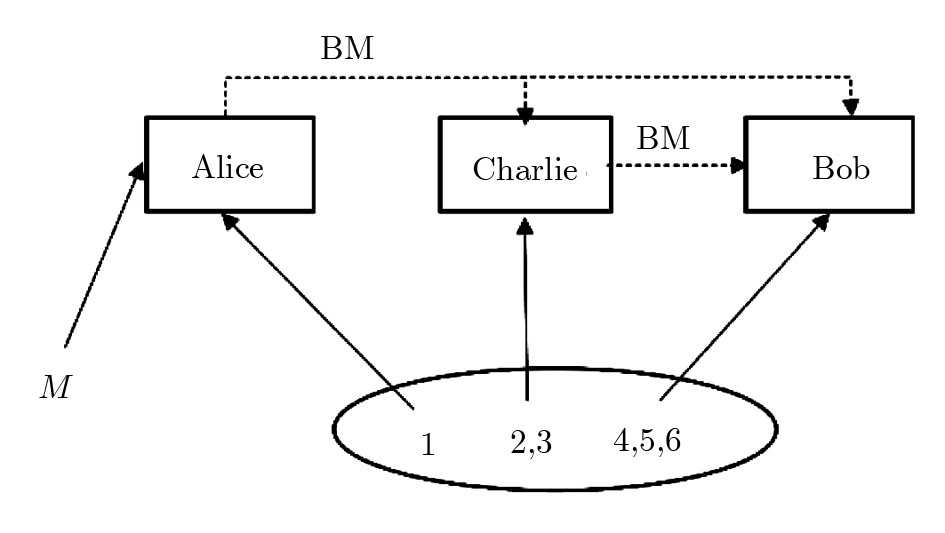
Our quantum multi-proxy blind signature is based on controlled teleportation, which takes a genuinely entangled six qubits as its quantum channel. It is given by
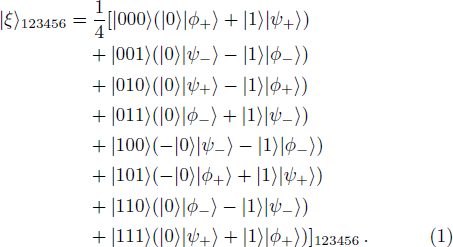
Suppose that the quantum state of particle M carrying message in Alice is
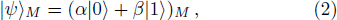
The system quantum state composed of particle M and particles (
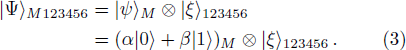
(i) Alice performs Bell state measurement on particles M and 1. The measurement will collapse the state of |ψ〉M123456 into one of the following states

(ii) If Charlie agrees Alice and Bob to complete their teleportation, he performs Bell state measurement on particles (
Suppose that Alice’s measurement outcome is 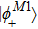
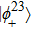
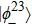
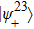
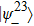
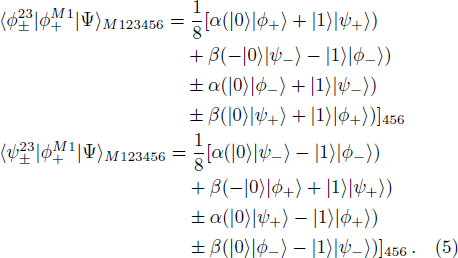
Then Charlie sends his measurement result to Bob.
(iii) Bob performs Bell-state measurement on particles (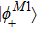


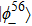
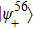
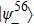
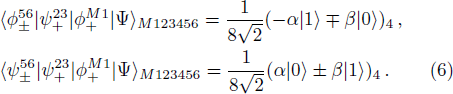
According to Alice’s, Charlie’s measurement outcomes, Bob performs an appropriate unitary operator on particle 4 to rebuild the original state |ψ〉M. For example, when particle 4 is in the state of Eq. (
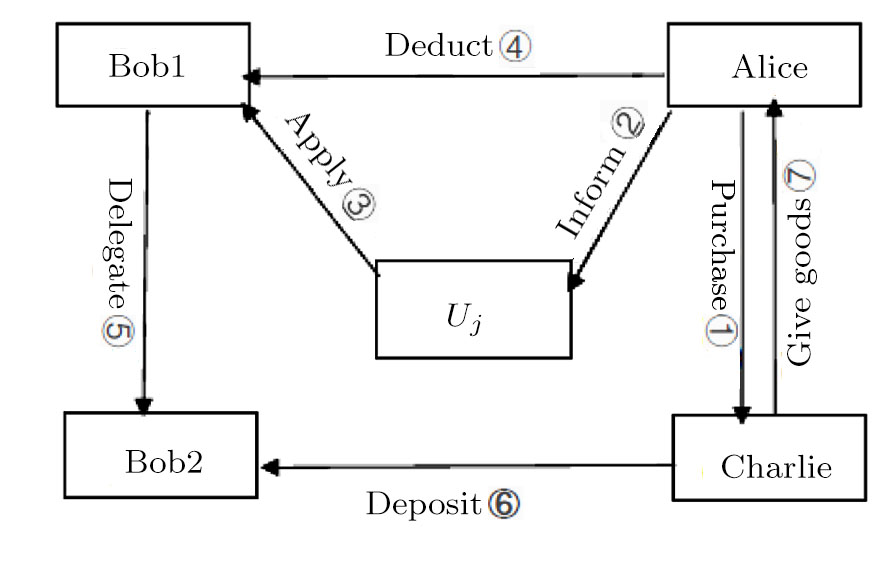
To clarify our mobile quantum E-payment system, five characters are defined as follows:
(i) Alice: the customer.
(ii) Bob1: the bank where Alice opens her account.
(iii) Uj: one number of the mobile terminals (j = 1,2,. . .,t).
(iv) Charlie: the merchant.
(v) Bob2: the bank where Charlie opens his account.
As shown in Fig.
The detailed procedure of our scheme can be described as follows.
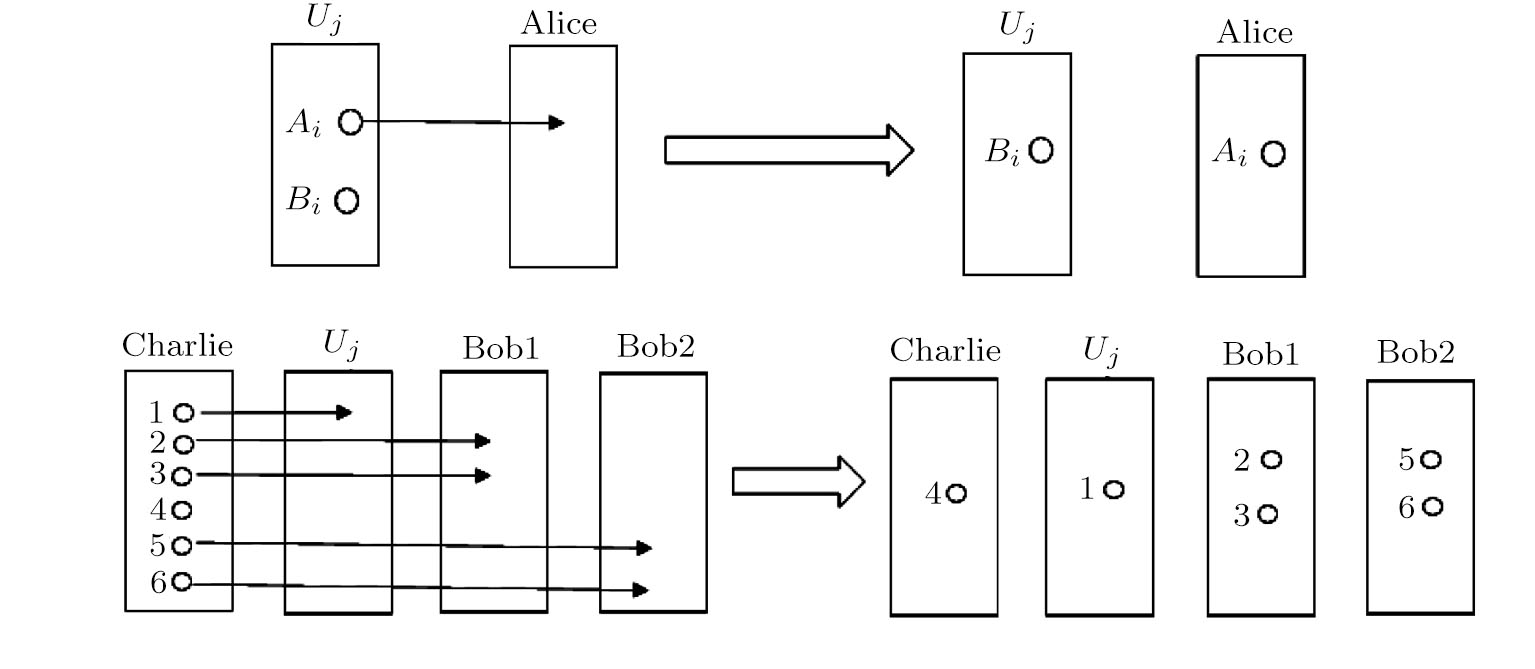
| Table 1 The measuring and encoding rules for quantum states. . |
In this section, we will prove that this scheme satisfies the properties of blindness, unforgeability, undeniability, and unconditionally security.
In the whole transaction, the message M2 has been transformed into 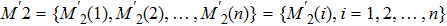
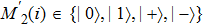
In our scheme, the bank Bob1 and Bob2 are trusty. In the following, we prove that it is impossible for anyone to forge signature. Suppose that Eve wants to forge Uj’s signature, he has to get the key KB1Uj. However, KB1Uj is distributed via QKD protocols, which have been proved unconditionally security. That is, Eve’s forgery can be avoided. Similarly, the original bank Bob1’s proxy certificate and Bob2’s signature can not be forged either.
In the following, we will show that our scheme is secure against the denial of both customer Alice and merchant Charlie. First of all, Alice has to encrypt her partial message M1 with the key KAUj and send it to Uj, Uj could gain M1 to identify Alice in case of disputes. Thus, Alice can not deny her purchase message M1. In addition, according to Subsec.
Our protocol’s unconditional security is ensured from the following aspects. First, we use the unconditionally secure QKD protocols for quantum key distribution. Second, we employ one-time pad to encrypt. Third, we arrange eavesdropping checks to achieve the secure quantum channel.
In this paper, we propose a practical E-payment protocol based on quantum multi-proxy blind signature. Compared with the previous works,[9–12] our scheme has some advantages. Firstly, our scheme could not only implement mobile E-payment but also realize the inter-bank payment. Secondly, our protocol has arranged eavesdropping checks to ensure a stronger security. Thirdly, our scheme only relies on Bell state measurement which is easy to implement with current technologies and experimental conditions. However, the received state’s fidelity may reduce because of the experimental environment,[19–20] with the development of the quantum information technique, our protocol can be applied successfully.
| [1] | |
| [2] | |
| [3] | |
| [4] | |
| [5] | |
| [6] | |
| [7] | |
| [8] | |
| [9] | |
| [10] | |
| [11] | |
| [12] | |
| [13] | |
| [14] | |
| [15] | |
| [16] | |
| [17] | |
| [18] | |
| [19] | |
| [20] |