† Corresponding author. E-mail:
In order to protect the privacy of query user and database, some QKD-based quantum private query (QPQ) protocols were proposed. Unfortunately some of them cannot resist internal attack from database perfectly; some others can ensure better user privacy but require a reduction of database privacy. In this paper, a novel two-way QPQ protocol is proposed to ensure the privacy of both sides of communication. In our protocol, user makes initial quantum states and derives the key bit by comparing initial quantum state and outcome state returned from database by ctrl or shift mode instead of announcing two non-orthogonal qubits as others which may leak part secret information. In this way, not only the privacy of database be ensured but also user privacy is strengthened. Furthermore, our protocol can also realize the security of loss-tolerance, cheat-sensitive, and resisting JM attack etc.
SPIR (symmetrically private information retrieval) is proposed to solve the problem in which user queries certain item of N items owned by database. In addition, it is also required that user cannot get other items and database cannot know which item user wants to get. While the two sides without trust are communicating, they want to not only prevent the common privacy from being eavesdropped but also protect the personal privacy.
The security of most traditional SPIR schemes is based on unproven assumptions of mathematical difficulty. However, with the rapid development of quantum computation, they are facing with more and more severe challenges.
QPQ protocol is the quantum solution of SPIR problem and the security is ensured by unconditional security theoretically in terms of physical principles. In QPQ protocols, an asymmetric key is generated between the user and database. The database knows the key all while the user only knows a little fraction. But the database has no idea about which part of the key the user knows. Using the asymmetric key, SPIR problem can be solved. Jakobi et al. proposed the first QKD-based QPQ protocol (J protocol).[1] It was based on SARG04 scheme,[2] and solved the problem of lacking support for large database. From then on, more and more researches focus on QKD-based QPQ protocols. Meanwhile, many improved protocols have been proposed.[3–23]
The factors that influence security of QPQ protocols are divided into external factors and internal factors. The attack from participants is usually more crucial than that from external part for a protocol. Thus a protocol needs to make sure that the common privacy is invulnerable to external factors, more importantly, it needs to ensure the personal privacy even if both sides of communication are dishonest, because they may cheat each other by sending a faked internal state or make a fake announcement to invade data privacy of the other side.
However, there is not any protocol could ensure the privacy of both user and database in previous QKD-based QPQ protocols. According to the one who prepares initial qubits, previous protocols can be divided into two categories. One is database Bob prepares initial qubits, while the other is user Alice prepares initial qubits.
Most of previous QKD-based QPQ protocols[1,4–21] use approach that Bob prepares and sends initial qubits thus with relative lower user privacy. Take J protocol[1] as an example. In this protocol, Database Bob sends qubits firstly and makes correlative classical announcement after Alice has received. As a result, this protocol has shortage of internal attack from database.[22] Bob can have higher probability to know the information about the bit locations of Alice by easily preparing a fake state. Thus the user privacy is threatened. Yang et al.[9] also proposed a protocol in which Bob prepares and sends initial photons in state 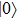
In addition, Wei et al.[18] proposed a protocol in which Bob makes quantum state to resist JM attack. In her protocol, user could not control the manipulations which Bob does on the signal. The reason is that individual attack of Bob may threaten user privacy and the protocol does not detect his cheating behavior. This also shows Wei’s protocol has some defects for user privacy. Thus, it can be inferred that, in the protocols which Bob makes initial state, it is very likely for Bob to launch internal attack because Bob knows the information about initial state accurately. In this paper we take J protocol as the representative of this kind of protocols to compare with our protocol.
Others ensure user privacy by using approach that Alice prepares initial quantum qubits, but there are some defects for, database security. For example, Yu et al.[22] proposed an improved J protocol against internal attack from database Bob and can enhance user privacy. In their protocol, the initial qubits are sent by Alice instead of Bob. So the database cannot know any information of initial quantum states. By this way, if Bob wants to implement internal attack, he can only infer initial quantum state according to outcome state and further make a fake announcement to get the bit locations of Alice. The user privacy has been greatly enhanced and then the threat of Bob’s attack is reduced. Moreover, together with honesty checking, the cheats of Bob can be detected and then be well resisted. However, this modification was at the cost of losing part of database privacy. By preparing fake states, Alice can get more final keys than normal condition after post-processing. In addition, there is no detection for cheating of Alice. Thus the database privacy will be threatened. Another protocol in which Alice prepares initial qubits is Yang’s protocol. It adds detection of database and cancels detection of user. Yang’s protocol[23] has discussed that the user privacy could be enhanced if the initial quantum states are made by Alice. Yang thinks the user privacy of their protocol is perfect, because the initial quantum states are made and transmitted by Alice. And according to Heisenberg uncertainty principle, Bob cannot get any information about the state.
In fact, however, although Bob cannot get any information about the state and thus improve the user privacy, user privacy is not perfect. This is because Bob will measure the quantum state after received it, he can infer initial state with certain probability, launch an internal attack and gain benefit. What is more, it costs nothing for Bob to do so because there is no detection for his cheating, which influences protocol’s user privacy. Therefore, the detection for cheating from database is added to our protocol. Thus we could not only provide a better user privacy but also detect external attack. In this paper, when comparing protocols in which Alice prepares initial qubits, we primarily discuss representative protocol, Yu’s protocol.
To enhance the privacy of both sides, we proposed a two-way-four-state-QKD-based QPQ protocol. In our protocol, the fake state attacking of Alice is useless thus it can ensure database security. Because the initial state is made by Alice, the user privacy is similar to Yu’s protocol[22] (the protocol with best user privacy of present four-state-QKD-based QPQ protocols), together with the detection for cheating from database, it can ensure high user privacy.
The rest of this paper is organized as follows. In Sec.
This protocol meets loss tolerance. Bob operates the two modes in this protocol in order to meet loss tolerance. When Alice received photon from Bob, she could not realize which results are necessary before she received announcement of Bob. For example, Alice prepares initial qubit 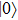
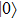
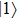
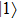
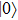
In addition, our protocol is also cheat-sensitive. Bob’s cheating behavior will also be found by Alice in Step 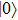
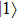
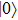
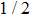
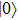
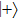
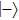
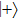
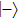
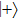
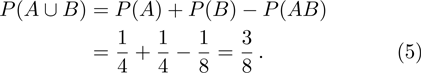
Similarly, if Bob announces 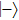
Bob will state 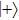
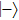
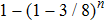
For Yu’s protocol,[22] the lowest probability that Bob’s cheating will be detected by Alice is 1/4 which is lower than ours. The reason is that Bob announces outcome state while the value of bit in our protocol. Thus our protocol is super to Yu’s protocol[22] in cheat-sensitive.
The protocol uses the post-processing similar as Yang’s protocol,[23] which can make the protocol resist joint-measurement attack.
In present protocols that Alice sends initial states, Alice can threat the security of database by preparing fake states. But in our protocol, Alice derives the key bit by comparing initial quantum state and outcome state of quantum returned by database, Alice’s fake states are useless and fake state attack is avoided. The detailed analysis is described as follows:
Assume that Alice is dishonest, she can prepare a fake quantum state 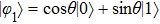
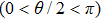
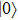
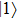
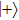
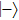
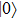
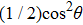
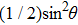
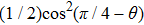
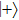
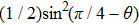
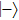
Assuming that Alice uses Z base to measure her qubit after she received from Bob, the results could be 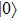
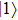
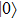
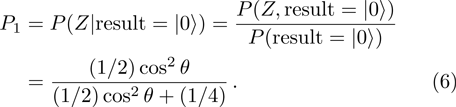
Obviously, the value reached maximum when θ = 0, 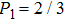
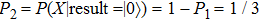
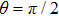
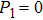
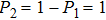
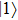
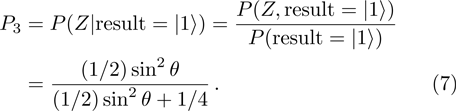
Obviously, the value reached maximum when 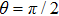
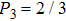
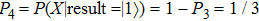
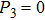
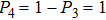
In conclusion, in order to get more items of qubits, Alice needs to get maximum probability of Bob’s measuring base. That is, she will use 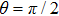
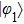
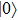
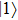
Similarly, if Alice uses X base to measure, maximum probability of Bob’s measuring base she could obtain only when she sends 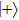
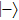
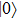
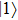
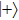
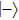
Compared with J protocol, if state received by Alice is 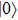
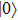
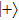
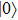
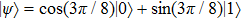
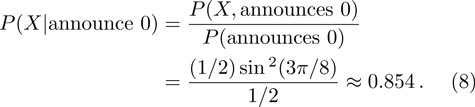
And if Bob announces 1, then the probability that Bob uses Z base to measure is:
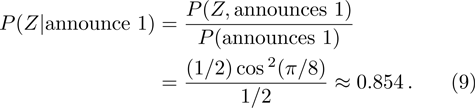
It means that Alice can greatly improve the possibility of getting bits by preparing fake states, so Alice can get more bit of final key. Obviously, our protocol has higher database security comparing to Yu’s protocol.[22]
Alice is likely to use the strategy of faking EPR-pair in order to get more items. She could prepare state 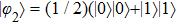
If Bob chooses Ctrl mode, Alice will have two photons with same state after Bob returning his photon. At this moment, if Alice uses Z base to measure a photon and the outcome state is 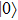
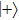
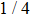
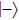
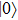
For Shift mode, Alice transfers the outcome state of the returned photon. Thus the Shift mode will be consistent with Ctrl mode, the same security can be ensured.
In our protocol, if the outcome state which Bob has got was 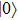
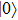
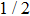
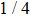
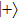

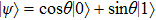
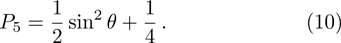
It reaches maximum (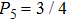
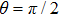
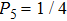
It also proves that, after Alice prepared initial state, the threat of Bob’s spoofing is greatly reduced because Bob could not get the information of initial state accurately.
We propose a new QPQ protocol in this paper which Alice prepares and sends quantum states to improve user privacy. What is more, it also uses specific two-way communication approach in which Bob returns measured quantum state by Ctrl or Shift mode instead of announcing two non-orthogonal qubits, which may leak half of the correct qubit, so the database security of ours is also strengthened. By comparing our protocol with some protocols in which Bob prepares initial qubits and protocols in which Alice prepares initial qubits, it can be showed that our protocol is better for both user privacy and database security.
(i) It has high database security compared with other QPQ protocols in which Alice initializes qubits. In our protocol, it is useless to get more key bits for Alice by sending fake qubits. So the database security has been significantly improved.
(ii) The initial quantum states are generated by Alice while Bob cannot know the exact information, thus user privacy of this protocol is improved as well. What is more, the user privacy is strengthened by checking process of internal attacking behavior of Bob.
(iii) It can resist JM attack because of the post-processing methods proposed by Yang’s protocol.[23]
As a two way QPQ protocol, of course, it has a little more complicated compared with its counterparts of one way protocols, while enhancing the security of both parts of communications. Similar to many present QPQ protocols which based on QKD protocol, our protocol also has not solved the problem that Alice always obtains more than one bit of the final key. We will continue to the research in the future.
| [1] | |
| [2] | |
| [3] | |
| [4] | |
| [5] | |
| [6] | |
| [7] | |
| [8] | |
| [9] | |
| [10] | |
| [11] | |
| [12] | |
| [13] | |
| [14] | |
| [15] | |
| [16] | |
| [17] | |
| [18] | |
| [19] | |
| [20] | |
| [21] | |
| [22] | |
| [23] |

